How to Authenticate Experience Cloud Users with Salesforce SSO
Alex Colburn – October 5, 2021

Salesforce Single sign-on (SSO) is a method of authentication that allows users to manage one set of credentials across multiple applications.
Think back to the first time you logged into your AIM account in ‘97. That login was burned into your brain, living rent-free in your memory. 20 years later, a lot of things have changed. Now you have more passwords than you know what to do with. You’ve created different variations over time, followed the special character rules, wrote them down on sticky notes, or swore to yourself that you’d remember it. At the same time, malware attacks have sky-rocketed and hackers are flying first-class with your personal data in tow. The information beyond the login page has become more important than ever to keep confidential - like your Salesforce org.
With single sign-on, Salesforce users can avoid defaulting to sticky notes or memory games and finally break up with the dreaded ‘forgot password?’ process. They'll also benefit from easier onboarding and offboarding processes.
In this article, we’ll dive into how Salesforce SSO will benefit organizations and how developers can authenticate Experience Cloud users.
Benefits of SSO for Salesforce
As Salesforce states in their documentation, “Single sign-on (SSO) is an authentication method that enables users to access multiple applications with one login and one set of credentials.” This process allows you to log into your org and automatically access all apps without using different usernames and passwords for each one. On top of preventing the headache of resetting passwords every 90 days, it makes the platform more seamless and secure.
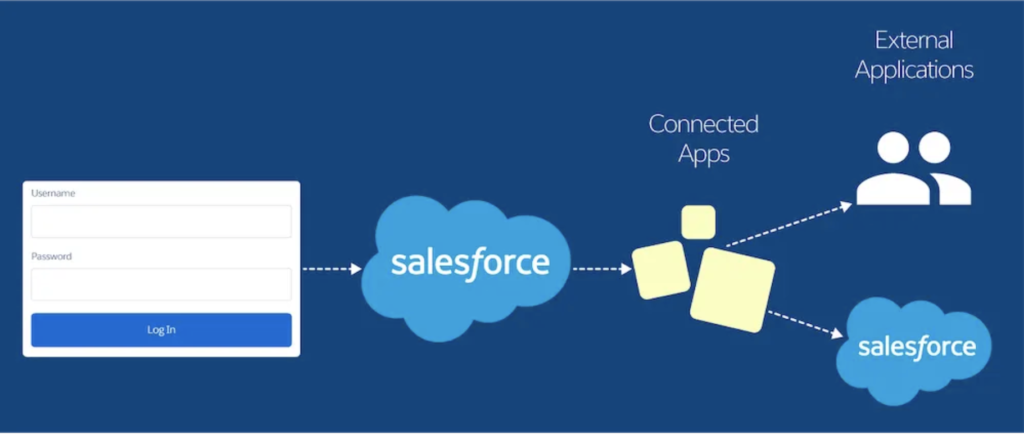
SSO can be configured to allow:
- Users to log in from a third-party application, like a corporate portal
- External users to login
- Organizations that uses Okta or Microsoft Azure to easily it set up in Salesforce
A Salesforce consultant at Digital Mass shared a great example in this episode of The Developers Speak, focused on authenticating external users to access their client’s Experience Cloud page.
Authenticating External Experience Cloud Users
We get a lot of questions about managing and authenticating external users in Salesforce, especially in Experience Cloud. This is because Experience Cloud is used to bridge the gap between internal and external users sharing relevant data.
When it comes to authenticating external users in Experience cloud, you have a couple of options.
- If they belong to an organization that has an authentication provider like Okta or Microsoft Azure, set up SSO in the Experience Cloud page via SAML assertions by exchanging information between orgs.
- Or, you can set up OpenID Connect to allow users to login with any third party application that implements the server side of OpenID Connect’s protocol.
But sometimes documentation can’t keep up with its own ever-changing landscape. As Tom shared, there’s a secret sauce to customizing the experience for external users in Experience Cloud.
What’s not in the Salesforce documentation
Additional steps will need to be taken if you're authenticating a custom experience for external users from multiple companies.
- Take your Experience Cloud login URL and swap it with your Salesforce instance URL in all areas that Okta or Miscrosoft Azure would require your Salesforce instance URL.
- Put the Experience Cloud login URL in every field, except for the audience restriction, which you should keep as your Salesforce instance URL.
Parting Thoughts
With Salesforce SSO, users can log in to all the apps they need to, easily and securely. With single sign-on, Salesforce users can finally avoid defaulting to sticky notes, memory games, and the dreaded ‘forgot password?’ process while keeping your org’s security at an all-time high.
If you’d like to talk about more of the advantages of Salesforce SSO with Digital Mass’ team of certified Salesforce consultants, contact us.